level 5
Mission Description
Cross-site scripting isn't just about correctly escaping data. Sometimes, attackers can do bad things even without injecting new elements into the DOM.
Mission Objective
Inject a script to pop up an alert() in the context of the application.

sign up을 누르면 이렇게 나온다.
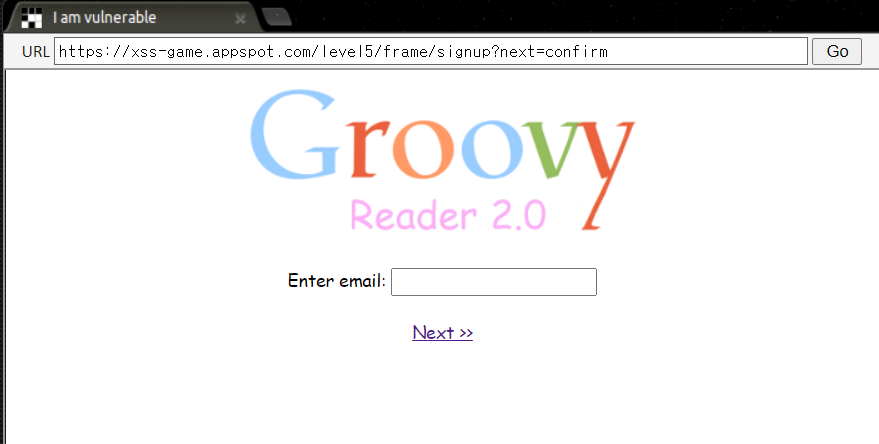
이메일을 입력하고 next를 누르면 몇 초 뒤에 처음 페이지로 돌아간다. url은 next=confirm으로 바뀌었다.
힌트
더보기
- The title of this level is a hint.
- It is useful look at the source of the signup frame and see how the URL parameter is used.
- If you want to make clicking a link execute Javascript (without using the onclick handler), how can you do it?
- If you're really stuck, take a look at this IETF draft
힌트도 보니 next=confirm 부분을 이용하는 것은 맞는 것 같다.
코드를 보자.
confirm.html
<!doctype html>
<html>
<head>
<!-- Internal game scripts/styles, mostly boring stuff -->
<script src="/static/game-frame.js"></script>
<link rel="stylesheet" href="/static/game-frame-styles.css" />
</head>
<body id="level5">
<img src="/static/logos/level5.png" /><br><br>
Thanks for signing up, you will be redirected soon...
<script>
setTimeout(function() { window.location = '{{ next }}'; }, 5000);
</script>
</body>
</html>signup.html
<!doctype html>
<html>
<head>
<!-- Internal game scripts/styles, mostly boring stuff -->
<script src="/static/game-frame.js"></script>
<link rel="stylesheet" href="/static/game-frame-styles.css" />
</head>
<body id="level5">
<img src="/static/logos/level5.png" /><br><br>
<!-- We're ignoring the email, but the poor user will never know! -->
Enter email: <input id="reader-email" name="email" value="">
<br><br>
<a href="{{ next }}">Next >></a>
</body>
</html>링크 주소가 next변수의 값으로 전달된다. next 값을 조작해 공격하는 것 같다.
welcome.html
<!doctype html>
<html>
<head>
<!-- Internal game scripts/styles, mostly boring stuff -->
<script src="/static/game-frame.js"></script>
<link rel="stylesheet" href="/static/game-frame-styles.css" />
</head>
<body id="level5">
Welcome! Today we are announcing the much anticipated<br><br>
<img src="/static/logos/level5.png" /><br><br>
<a href="/level5/frame/signup?next=confirm">Sign up</a>
for an exclusive Beta.
</body>
</html>
자바스크립트를 이용하자.
javascript:alert('xss');

저렇게 입력하고 next를 눌렀더니 공격에 성공했다.

'Web Hacking > XSS game' 카테고리의 다른 글
| [XSS] XSS game level 6 (0) | 2021.02.22 |
|---|---|
| XSS game level 4 (0) | 2021.02.07 |
| [XSS] XSS game level 3 (0) | 2021.01.31 |
| [XSS] XSS game Level 2 (0) | 2021.01.30 |
| XSS game Level 1 (0) | 2021.01.17 |